LIA Update: Bare Metal Sandbox Deployment for Payload Execution
In September, we mentioned that new features were in the works, and we are excited to share that they are now live. Over the past few months, we have focused heavily on backend improvements and enhancing our existing analysis pipeline. A major part of this effort has been the addition of a new sandbox environment that helps us extract more value from the payloads sourced from tracked families. As a result, our pipeline now includes a true bare-metal sandbox where all downloaded payloads are automatically submitted for analysis, expanding the detection surface and giving you more data to pivot from.
No Virtualization, No Problems
Malware commonly attempts to detect virtual environments and analysis tools to evade identification. Hardening virtualized sandbox environments has become a constant cat-and-mouse game, so we chose to eliminate virtualization entirely and instead deploy real hardware.
This drastically reduces the detection surface that malware can use to determine whether it is running in an analysis environment.
These machines are fully Internet-connected, allowing malware to phone home and retrieve additional payloads or commands. More details on our deployment are available in our intel cable (login required).
Additional Updates
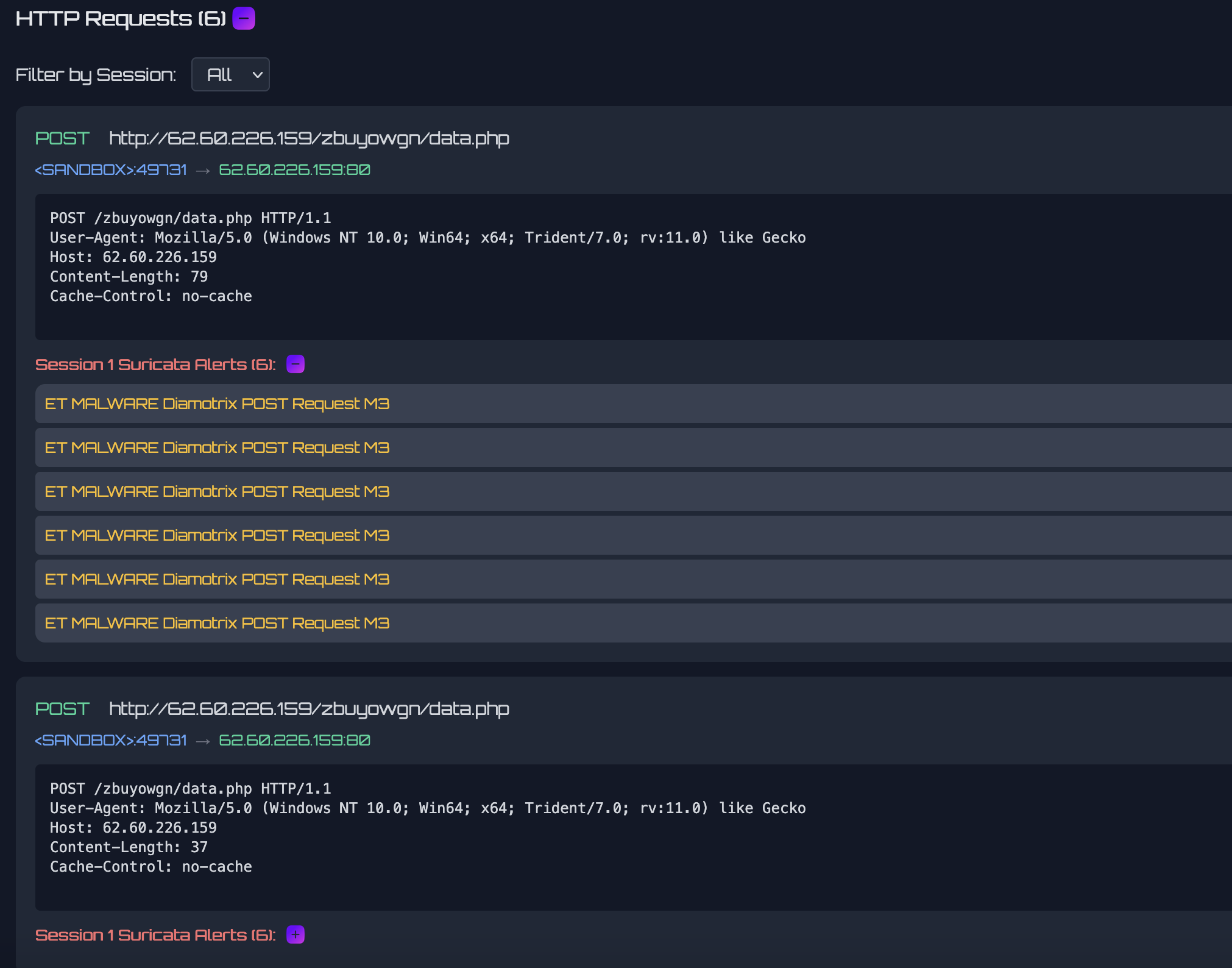
Beyond the new sandbox, we have improved the user experience and enhanced how data is displayed. Communication logs from the sandbox are searchable, enabling hunting by domain, IP, or full URL, even if a payload was not detected during execution. An example of HTTP requests captured during an sandbox run is shown below.
We have also expanded the statistics available for individual botnets, going beyond the 30-day lookback window provided to free users.
More Details
Please log in to read more in-depth about the update, including further details about the sandbox environment.